【安全资讯】多模块僵尸网络Prometei利用SMB传播
研究人员最近发现一起复杂的攻击活动,其使用了一个名为Prometei的多模块僵尸网络,并通过多种方式进行传播,例如使用被盗凭据的SMB、psexec、WMI和SMB漏洞,最终在受害机器上挖取门罗币获取经济收益。感染开始于僵尸网络主文件,该文件通过SMB从其它受感染系统中复制,使用修改后的Mimikatz模块获取密码和永恒之蓝等漏洞。Prometei有超过15个可执行模块,所有模块都由主模块下载和驱动,主模块通过HTTP与命令和控制(C2)服务器持续通信。
该僵尸网络有两个主要功能分支,这两个分支可以独立运行。
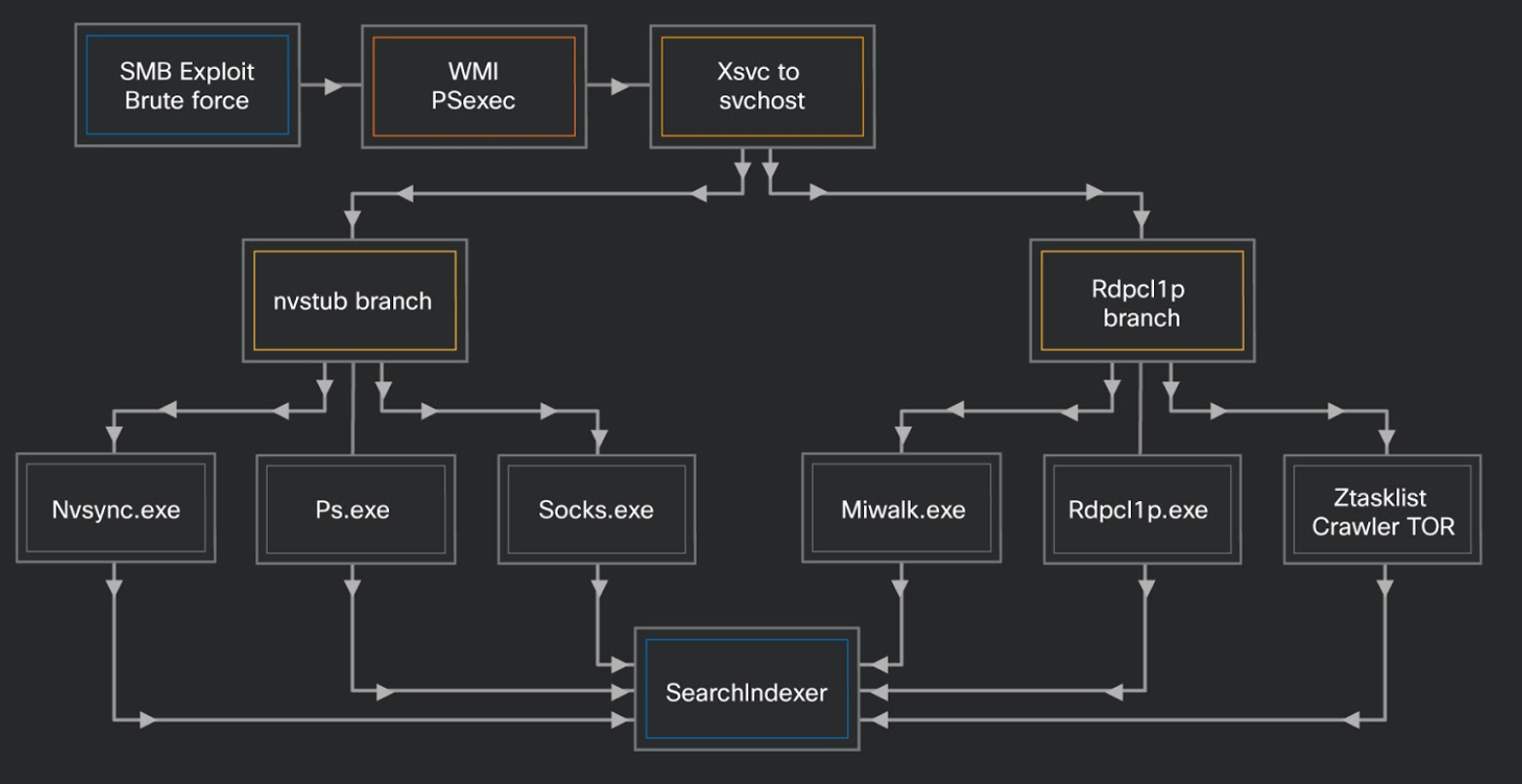
( Prometei 的两个主要分支)
一旦主机被感染称为僵尸网络,主控制就会进入来自C2的无限循环等候命令,以下命令使攻击者可以控制受感染的系统:
run — Execute a program/file using ShellExecute API
exec — Execute a program using CreateProcess API
srun — Check if the path exists, calculate its SHA1 and execute using CreateProcess
cmdt — Launch a command shell, redirect stdin and stdout to pipes over HTTP
cmd — Launch a command shell, redirect stdin and stdout to pipes over HTTP
scmd — Execute a single command
ver — Get the bot's version
extip — Get the bot's external IP address
enc — Get/set the RC4 encryption key
updatev3 — Download updated bot to svchost2.exe and start the process then remove the file. If that is not successful terminate the process first.
set_timeout — Set period for connecting to C2 server
set_cc — Set new C2 server
touch — Open file and write a single byte to change checksums and access times
wget — Download file
xwget — Download file, save it, then open it and XOR it using single byte XOR with initial key 0x42 and addition of 0x42 for each byte
stop_mining — Terminate the mining process by calling cmd.exe /C taskkill -f -im SearchIndexer.exe. If that did not work, try launching a thread that will call taskkill.
start_mining1 — Read C:\windows\dell\Desktop.dat to get parameters and launch SearchIndexer.exe
start_mining — Request desktop.txt from the C2, save it to Desktop.dat and launch the miner with parameters read from Desktop.dat
quit — Terminate the bot using TerminateProcess
quit2 — Exit the command handler loop without calling TerminateProcess
getinfo — Get information about the infected system using WMI WQL queries and other methods
该僵尸网络的算力速度在700KH / sec和950KH / sec之间,这意味着受感染的系统数量很少。在其为期四个月的运行中,其收入平均不到5,000美元,或每月平均1,250美元。
Prometei在今年三月就处于活跃状态,除了窃取计算能力外,僵尸网络窃取和验证凭据的行为令人担忧。尽管我们仅看到证据表明盗用的凭证被用于横向传播,但它们在地下市场也具有价值,丢失重要的管理用户名和密码的潜在损失非常高。





